Container Architecture
Containers have gained so much popularity in recent years. However, the technology behind containers has been around for long time. In 2001, Linux introduced a project named VServer. VServer was the first attempt of complete sets of running processes inside a single server with a high degree of isolation. The idea of isolated processes further evolved and became formalized after VServer success. Now we discuss Container Architecture in this article.
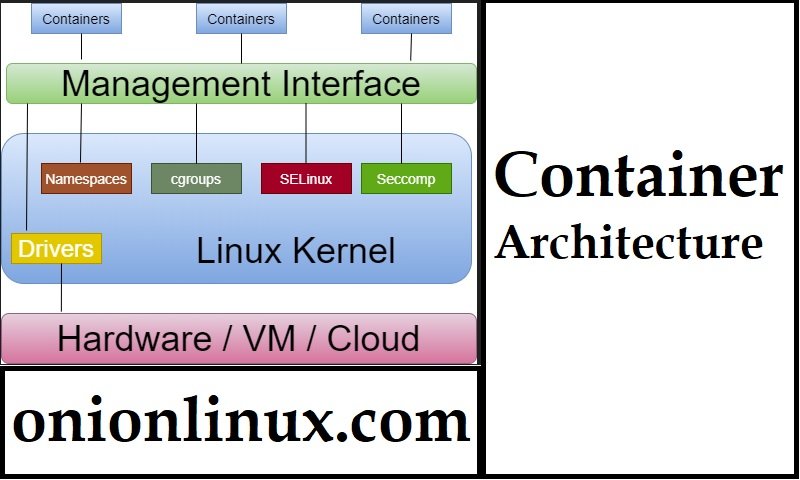
Features of Linux Kernel involved to make containers isolated
Namespaces
Kernel can isolate specific system resources, by placing the resources within a namespace and it is usually visible to all processes. Processes that are members of that namespace only can see the resources in a namespace. Namespaces can include resources like network interfaces, the process ID list, mount points, IPC resources, and the host name information.
Control groups (cgroups)
Control groups manage and limit the resources of processes and their children. Control group restricts the amount of system resources that might used by processes. Those restrictions keep one process from using too many resources on the host.
Seccomp
It was developed in 2005 and introduced to containers circa in 2014, Seccomp is a linux kernel feature that limits how processes could use system calls. Seccomp defines a security profile for all processes for whitelisting the system calls, parameters and file descriptors they are allowed to use.
SELinux
SELinux (Security-Enhanced Linux) is linux kernel security module used for mandatory access control system for processes. Linux kernel uses SELinux to protect processes from each other and to protect the host system from its running processes. Processes run as a confined SELinux type that has limited access to the system resources.
An important use case of containers is having several replicas of the same service (for example, a web server) in the same host machine. Each replica has isolated resources (i.e file system, ports, memory etc), so there is no need of the service to handle the resource sharing. Isolation guarantees that a harmful service or malfunctioning does not impact other services or containers in the same host, nor in the underlying system.
All of these container features focus around a basic concept: enabling processes to run isolated while still accessing system resources. This is the fundamental concept of container technology and the basis for all container implementations.
Container is a process with restrictions. Instead of running a single binary file, a container runs an image. An image is a bundle of file-system that contains all dependencies required to execute a process: files in the file system, installed packages, kernel modules, running processes, and available resources. Container images are files with multiple instructions, packages, dependencies, they can be managed by versioning systems for improving automation on container and image provisioning. like executable files are the foundation of a running process similarly images are the foundation of running container.
Usually Container images are stored and maintained in an image repository but images needs to be available locally for container runtime to execute them.An image repository could be public or private, where images can be stored, searched and retrieved. Other features of image repositories are remote access, image metadata, authorization or image version control.
Different Image Repositories
There are different Image Repositories available and each repository offers different features:
- Docker Hub
- Red Hat Quay
- Red Hat Container Catalog
- Google Container Registry
- Amazon Elastic Container Registry
To manage and deploy these container, we use Orchestration tools, there are many Orchestration tools available.
Container Orchestration
It is the process of automating the management of container-based microservice applications across multiple clusters. It manages the lifecycles of containers, especially in large, dynamic environments.
Container Orchestration task:
- Provisioning and deployment of Containers
- Scale up or scale down containers to spread application load evenly across host infrastructure
- Redundancy and availability of Containers
- Movement of containers from one host to another host in case of resource shortage in a host, or if a host dies
- Exposing the ports and services running in a container with the outside world, according to the requirements
- Allocating and deallocating resources between containers
- Load balancing of services between the containers
- Configuring the application in relation to the containers running it
- Health monitoring of containers and hosts
- Deployment of containers
List of some popular Orchestration Tools
Kubernates
It is best suited for enterprise-level Containers Orchestration and cluster management, it provides tremendous amount of functionality. There are various platforms which manages Kubernates like Google, AWS, Azure, Pivotal, and Docker.
Docker Swarm
Docker Swarm is more suitable for those who are already familiar with Docker Compose. It is simple and straightforward it doesn’t requires any additional software. However, unlike Kubernetes and Amazon ECS, Docker Swarm does not have advanced functionalities like built-in logging and monitoring. Therefore it is more suitable for the small scale organization or those who are getting started with containers.
Amazon ECS
Deploying and configuring cluster using Amazon is very easy and fast, so it is fast and convenient way to start-up and meets demand with scale, it integrates with several other AWS services. it’s ideal for small teams who do not have many resources to maintain containers.
One of its drawback is that it’s not suitable for nonstandard deployments. It also has ECS specific configuration files, so it is very difficult to troubleshoot the problems.
RedHat OpenShift
Red Hat OpenShift Container Platform (RHOCP) is a set of modular components and services built on top of a Kubernetes container infrastructure. It adds the capabilities to provide a production PaaS platform such as remote management, multitenancy, increased security, monitoring and auditing, application life-cycle management, and self-service interfaces for developers.
OpenShift Features
OpenShift adds the following features to a Kubernetes cluster:
Integrated developer workflow
RHOCP integrates a built-in container registry, CI/CD pipelines, and S2I; a tool to build artifacts from source repositories to container images.
Routes
Easily expose services to the outside world.
Metrics and logging
Include built-in and self-analyzing metrics service and aggregated logging.
Unified UI
OpenShift brings unified tools and a UI to manage all the different capabilities.
I hope you like this post, if you have any questions? please leave comment below!
Thanks for reading. If you like this post probably you might like my next ones, so please support me by subscribing my blog.

Pingback: Building Container Image using Dockerfile — OnionLinux %
Pingback: Architecture of Kubernetes & OpenShift — OnionLinux